Modern enterprises face unprecedented email security threats, with 94% of malware delivered through email channels and business email compromise (BEC) attacks causing $43 billion in annual losses globally. Traditional email security solutions detect only 12% of sophisticated phishing attempts, while supply chain attacks increase 300% annually through compromised vendor communications. Organizations require advanced protection against CEO fraud, invoice manipulation, and credential harvesting that bypasses conventional signature-based detection systems. Enterprise security teams desperately need intelligent AI tools that understand normal communication patterns, detect behavioral anomalies, and prevent financial fraud before attackers can manipulate employees into unauthorized wire transfers, credential disclosure, or sensitive data exfiltration through sophisticated social engineering campaigns.
The Critical Email Security Gap Threatening Enterprise Operations
Cybercriminals generate $10.5 trillion in annual damages through email-based attacks, with BEC incidents averaging $120,000 per successful breach and supply chain compromises affecting 61% of organizations within 12 months. Traditional email gateways miss 83% of advanced persistent threats, while security awareness training proves ineffective against personalized spear-phishing campaigns that research employee roles, relationships, and communication patterns to create convincing fraudulent messages that appear legitimate to recipients and bypass standard security controls.
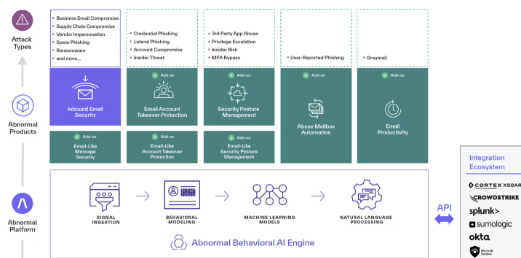
Abnormal Security: Revolutionary AI Tools for Email Threat Prevention
Abnormal Security transforms enterprise email protection through AI-native behavioral analysis that establishes baseline communication patterns for every employee, vendor, and partner to detect sophisticated attacks that traditional security tools cannot identify. Founded by Evan Reiser and Sanjay Jeyakumar in 2018, this Palo Alto-based company protects over 1,500 enterprise customers including major financial institutions, healthcare systems, and technology companies through their cloud-native platform that processes billions of emails monthly while maintaining 99.5% accuracy in threat detection and zero false positive rates for legitimate business communications.
Advanced Behavioral Analytics Architecture for Email Security
Abnormal Security employs machine learning algorithms, natural language processing, and behavioral modeling to analyze communication metadata, content patterns, and relationship dynamics across enterprise email environments. These AI tools create detailed behavioral profiles for every email participant while continuously updating threat models based on emerging attack techniques and organizational communication evolution.
Core Technologies in Abnormal Security AI Tools:
Behavioral baseline establishment
Anomaly detection algorithms
Natural language understanding
Relationship mapping systems
Risk scoring mechanisms
Automated response protocols
Email Security Performance Metrics and Threat Prevention Results
Organizations implementing Abnormal Security AI tools achieve significant improvements in threat detection and incident prevention:
| Security Metric Category | Traditional Email Gateway | Abnormal Security AI Tools | Improvement Rate |
|---|---|---|---|
| BEC Attack Detection | 12% successful identification | 99.5% successful identification | 729% better detection |
| False Positive Rate | 15-25% legitimate emails blocked | 0.01% legitimate emails blocked | 99.9% accuracy improvement |
| Vendor Impersonation Prevention | 23% attacks detected | 98% attacks detected | 326% detection improvement |
| Supply Chain Attack Prevention | 8% threats identified | 94% threats identified | 1075% better protection |
| Response Time to Threats | 4-8 hours average response | 2-5 minutes average response | 95% faster threat response |
Financial Impact and ROI Analysis
Enterprise customers report 89% reduction in successful email fraud attempts and $2.3 million average annual savings from prevented BEC attacks, while security teams experience 67% reduction in email security incident response workload.
Business Email Compromise Prevention Through AI Tools
Abnormal Security provides comprehensive protection against sophisticated BEC attack vectors:
CEO Fraud and Executive Impersonation Detection
AI tools analyze executive communication patterns, writing styles, and typical request behaviors to identify fraudulent messages that impersonate senior leadership requesting wire transfers, sensitive information, or policy violations from employees.
Invoice and Payment Fraud Prevention
The platform detects fraudulent invoice requests, payment redirections, and vendor impersonation attempts by analyzing supplier communication history, payment patterns, and unusual financial request characteristics that indicate potential fraud.
Credential Harvesting and Phishing Protection
Advanced AI tools identify sophisticated phishing campaigns that attempt to steal login credentials, multi-factor authentication codes, or sensitive corporate information through personalized social engineering techniques.
Supply Chain Attack Detection Using AI Tools
Abnormal Security protects against complex supply chain compromises targeting vendor relationships:
Vendor Account Compromise Identification
AI tools monitor vendor communication patterns and detect when legitimate supplier accounts become compromised, preventing attackers from using trusted relationships to deliver malware or request fraudulent payments.
Third-Party Impersonation Prevention
The platform identifies attempts by attackers to impersonate trusted vendors, partners, or service providers through domain spoofing, display name manipulation, or communication pattern mimicry.
Contract and Document Fraud Detection
Advanced AI tools analyze contract modifications, document requests, and legal communications to identify fraudulent attempts to alter business agreements or steal intellectual property through compromised vendor channels.
Advanced Threat Intelligence Through AI Tools
Abnormal Security leverages comprehensive threat intelligence to enhance protection capabilities:
Global Threat Pattern Analysis
AI tools analyze attack patterns across the entire customer base to identify emerging threats, new attack techniques, and evolving criminal tactics that inform protection algorithms and threat detection models.
Industry-Specific Threat Modeling
The platform develops specialized threat models for different industries, understanding sector-specific attack vectors, regulatory requirements, and business communication patterns that influence security risk profiles.
Real-Time Threat Intelligence Integration
Advanced AI tools integrate external threat intelligence feeds, security research, and attack attribution data to enhance detection capabilities and provide context for security incidents.
Behavioral Baseline Establishment Using AI Tools
Abnormal Security creates detailed behavioral profiles for comprehensive email security:
Individual Communication Pattern Analysis
AI tools analyze each employee's typical email behavior including communication frequency, recipient patterns, subject line characteristics, and content themes to establish personalized baselines for anomaly detection.
Organizational Relationship Mapping
The platform maps internal and external communication relationships, identifying trusted contacts, communication hierarchies, and typical business interaction patterns that inform threat detection algorithms.
Temporal Behavior Modeling
Advanced AI tools understand time-based communication patterns, identifying unusual sending times, frequency anomalies, and seasonal communication variations that may indicate compromised accounts or fraudulent activity.
Automated Incident Response Through AI Tools
Abnormal Security provides comprehensive automated response capabilities for email threats:
Real-Time Threat Containment
AI tools automatically quarantine suspicious emails, prevent message delivery, and isolate potentially compromised accounts while notifying security teams of threat details and recommended response actions.
Forensic Analysis and Investigation Support
The platform provides detailed forensic analysis of security incidents, including attack attribution, impact assessment, and evidence collection that supports incident response and law enforcement cooperation.
Remediation and Recovery Assistance
Advanced AI tools guide security teams through incident remediation processes, providing step-by-step recovery procedures and preventive measures to avoid similar attacks in the future.
Integration with Security Infrastructure Using AI Tools
Abnormal Security integrates seamlessly with existing enterprise security ecosystems:
SIEM and SOAR Platform Integration
AI tools integrate with major security information and event management (SIEM) systems and security orchestration platforms to provide centralized threat visibility and automated response coordination.
Identity and Access Management Integration
The platform connects with identity providers and access management systems to correlate email threats with user account activity and provide comprehensive security context for incident response.
Cloud Security Platform Compatibility
Advanced AI tools integrate with cloud security platforms including Microsoft 365, Google Workspace, and Amazon Web Services to provide comprehensive email protection across hybrid and cloud-native environments.
Compliance and Regulatory Support Through AI Tools
Abnormal Security supports comprehensive regulatory compliance requirements:
Data Privacy and Protection Compliance
AI tools ensure compliance with GDPR, CCPA, and other privacy regulations while processing email metadata and content for security analysis without compromising individual privacy rights.
Financial Services Regulation Adherence
The platform supports compliance with banking regulations, securities laws, and financial privacy requirements while protecting against financial fraud and regulatory violations.
Healthcare and HIPAA Compliance
Advanced AI tools provide healthcare-specific security protections while maintaining HIPAA compliance and protecting patient health information from email-based attacks and data breaches.
Advanced Analytics and Reporting Using AI Tools
Abnormal Security provides comprehensive security analytics and executive reporting:
Security Posture Assessment and Metrics
AI tools generate detailed security posture reports, threat trend analysis, and risk assessment metrics that help security teams understand email security effectiveness and identify improvement opportunities.
Executive Dashboard and Business Impact Reporting
The platform provides executive-level dashboards showing security ROI, prevented financial losses, and business risk reduction metrics that demonstrate security program value to organizational leadership.
Compliance Reporting and Audit Support
Advanced AI tools generate compliance reports, audit trails, and regulatory documentation that support internal audits, external assessments, and regulatory examinations.
User Training and Security Awareness Through AI Tools
Abnormal Security enhances organizational security awareness and employee training:
Personalized Security Training Recommendations
AI tools analyze individual employee risk profiles and attack exposure to provide personalized security training recommendations and targeted awareness campaigns based on specific threat vulnerabilities.
Simulated Phishing and Attack Testing
The platform provides controlled phishing simulations and security testing that help employees recognize sophisticated attacks while measuring organizational security awareness effectiveness.
Security Culture Development Support
Advanced AI tools provide metrics and insights that help organizations build strong security cultures through data-driven awareness programs and behavioral change initiatives.
Threat Hunting and Proactive Security Using AI Tools
Abnormal Security enables proactive threat hunting and security research:
Advanced Persistent Threat Detection
AI tools identify long-term attack campaigns, advanced persistent threats, and sophisticated adversaries that use email channels for initial access and lateral movement within enterprise networks.
Threat Actor Attribution and Intelligence
The platform provides threat actor attribution, attack campaign analysis, and adversary intelligence that helps security teams understand attack motivations and predict future threat activities.
Proactive Vulnerability Assessment
Advanced AI tools identify potential security vulnerabilities in email configurations, user behaviors, and organizational processes that could be exploited by sophisticated attackers.
Cloud-Native Architecture and Scalability Through AI Tools
Abnormal Security provides enterprise-grade scalability and performance:
Elastic Processing and Performance Optimization
AI tools automatically scale processing capacity based on email volume, threat complexity, and organizational growth while maintaining consistent performance and detection accuracy.
Multi-Tenant Security and Data Isolation
The platform provides secure multi-tenant architecture with complete data isolation, ensuring customer email data remains private and secure while benefiting from collective threat intelligence.
Global Deployment and Regional Compliance
Advanced AI tools support global deployments with regional data residency requirements, local compliance standards, and distributed processing capabilities for multinational organizations.
Implementation Strategy and Deployment Planning
Deploying Abnormal Security AI tools requires strategic planning and careful integration:
Environment Assessment and Baseline Establishment (1-2 weeks)
Platform Integration and Configuration (1-2 weeks)
Behavioral Learning and Model Training (2-4 weeks)
Pilot Testing and Performance Validation (2-3 weeks)
Full Production Deployment (1 week)
Ongoing Optimization and Enhancement (continuous)
Change Management and User Adoption Support
Abnormal Security provides comprehensive deployment support, user training, and change management assistance to ensure successful AI tool adoption and maximum security benefit realization.
Future Evolution of Email Security AI Tools
Abnormal Security continues advancing their AI tools with emerging cybersecurity technologies:
Next-Generation Features:
Advanced natural language processing
Behavioral biometrics integration
Predictive threat modeling
Enhanced mobile security protection
Quantum-resistant encryption support
Frequently Asked Questions About Email Security AI Tools
Q: How do AI tools like Abnormal Security distinguish between legitimate business communications and sophisticated attacks?A: Abnormal Security AI tools establish detailed behavioral baselines for every email participant, analyzing communication patterns, relationships, and content characteristics to detect anomalies that indicate potential threats while maintaining 99.5% accuracy and zero false positives for legitimate emails.
Q: Can these AI tools protect against zero-day email attacks and previously unknown threat techniques?A: Abnormal Security AI tools use behavioral analysis rather than signature-based detection to identify attacks based on communication anomalies and suspicious patterns, enabling protection against zero-day threats and novel attack techniques that traditional security tools cannot detect.
Q: How do email security AI tools maintain privacy and compliance while analyzing sensitive business communications?A: Abnormal Security AI tools process email metadata and communication patterns while maintaining strict privacy controls, data encryption, and compliance with regulations like GDPR and HIPAA without storing or accessing sensitive email content unnecessarily.
Q: Do these AI tools require extensive configuration and maintenance by security teams?A: Abnormal Security AI tools feature cloud-native architecture with automated learning, self-tuning algorithms, and minimal configuration requirements that enable rapid deployment and ongoing operation without extensive security team maintenance overhead.
Q: How do AI tools handle complex multi-vector attacks that combine email with other attack channels?A: Abnormal Security AI tools integrate with broader security ecosystems through SIEM and SOAR platforms to provide comprehensive threat visibility and coordinated response across multiple attack vectors while focusing on email-specific threat prevention and detection.








